Wednesday, October 16, 2013
Something is broken in Blogger
Friday, February 8, 2013
Patch Adobe Flash Player NOW
Flash under attack, emergency patch issued: Update immediately | ZDNet
Adobe has issued an emergency fix for Flash to prevent two ongoing malware attacks against the world's most popular Web plug-in.US-CERT Current Activity
In an advisory note, Adobe announced the latest release of Flash Player 11.5, which will patch two security zero-day vulnerabilities that are actively being used by hackers and malware writers to spread malware.
Adobe Releases Security Advisory for Adobe Flash Player
Tuesday, December 11, 2012
A busy Patch Tuesday this December
What a busy Tuesday: Microsoft had a BIG Patch Tuesday compounded by Adobe's Patch Tuesday and Oracle's Patch Tuesday all at once. There are security patches for the Adobe Flash Players and Adobe AIR. Oracle issued a security-enhancing patch for Java JRE 7. There is an update for Java JRE 6, but it does not fix any security issues.
The SANS Diary entry for Microsoft lists many of the items, including an IE patch and a patch for Microsoft Word, as CRITICAL*, so you shouldn't delay patching past Friday if you use IE or Word.
- * Critical: Anything that needs little to become "interesting" for the dark side. Best approach is to test and deploy ASAP. Workarounds can give more time to test.
- ISC Diary | Microsoft December 2012 Black Tuesday Update - Overview
Overview of the December 2012 Microsoft patches and their status.
- It’s That Time of Year, For the December 2012 Bulletin Release - MSRC - Site Home - TechNet Blogs
... today we’re releasing seven bulletins, five Critical-class and two Important-class, addressing 12 vulnerabilities in Microsoft Windows, Internet Explorer (IE), Word and Windows Server. For those who need to prioritize deployment, we recommend focusing on the following two critical updates first: ....
- Microsoft fixes critical Windows 8, IE10 flaws for Patch Tuesday | ZDNet
Summary: Put a pot of coffee on, it's Patch Tuesday. Microsoft today released five critical patches that fix vulnerabilities in Windows 8 devices, including Surface tablets, and Internet Explorer 10.
Microsoft has released five critical security updates for Windows 8 and Windows RT in order to protect against a range of vulnerabilities identified in the recently released software.
All in all, there are seven updates for Windows users, with five rated "critical" that could lead to remote code execution, while two are rated "important," which fix flaws that could result in the operating system's security features being bypassed.
- Critical Updates for Flash Player, Microsoft Windows — Krebs on Security
Adobe and Microsoft have each released security updates to fix critical security flaws in their software. Microsoft issued seven update bundles to fix at least 10 vulnerabilities in Windows and other software. Separately, Adobe pushed out a fix for its Flash Player and AIR software that address at least three critical vulnerabilities in these programs.
A majority of the bugs quashed in Microsoft’s patch batch are critical security holes, meaning that malware or miscreants could exploit them to seize control over vulnerable systems with little or no help from users. Among the critical patches is an update for Internet Explorer versions 9 and 10 (Redmond says these flaws are not present in earlier versions of IE).
Articles on Adobe's Patches: (Note: the Krebs-on-Security article referenced above also discusses this)
- Adobe Security Bulletins Posted « Adobe Product Security Incident Response Team (PSIRT) Blog
Today, we released the following Security Bulletins:
- APSB12-26 – Security update: Hotfix available for ColdFusion 10 and earlier
- APSB12-27 – Security updates available for Adobe Flash Player
Customers of the affected products should consult the relevant Security Bulletin(s) for details.
- Adobe - Security Bulletins: APSB12-27 - Security updates available for Adobe Flash Player
Security updates available for Adobe Flash Player
Release date: December 11, 2012
Summary
Adobe has released security updates for Adobe Flash Player 11.5.502.110 and earlier versions for Windows and Macintosh, Adobe Flash Player 11.2.202.251 and earlier versions for Linux, Adobe Flash Player 11.1.115.27 and earlier versions for Android 4.x, and Adobe Flash Player 11.1.111.24 and earlier versions for Android 3.x and 2.x. These updates address vulnerabilities that could cause a crash and potentially allow an attacker to take control of the affected system.Adobe recommends users update their product installations to the latest versions:
- Users of Adobe Flash Player 11.5.502.110 and earlier versions for Windows should update to Adobe Flash Player 11.5.502.135.
- Users of Adobe Flash Player 11.5.502.110 and earlier versions for Macintosh should update to Adobe Flash Player 11.5.502.136.
- [ .... ]
- Users of Adobe AIR 3.5.0.600 and earlier versions for Windows should update to Adobe AIR 3.5.0.880.
- Users of Adobe AIR 3.5.0.600 and earlier versions for Macintosh should update to Adobe AIR 3.5.0.890.
Affected software versions
- Adobe Flash Player 11.5.502.110 and earlier versions for Windows and Macintosh
- Adobe Flash Player 11.2.202.251 and earlier versions for Linux
- Adobe Flash Player 11.1.115.27 and earlier versions for Android 4.x
- Adobe Flash Player 11.1.111.24 and earlier versions for Android 3.x and 2.x
- Adobe AIR 3.5.0.600 and earlier versions for Windows and Macintosh, Android and SDK (includes AIR for iOS)
To verify the version of Adobe Flash Player installed on your system, access the About Flash Player page,
or right-click on content running in Flash Player and select "About
Adobe (or Macromedia) Flash Player" from the menu. If you use multiple
browsers and did not select the option to 'Allow Adobe to install
updates' (Windows and Macintosh only), perform the check for each
browser you have installed on your system.
To verify the version of Adobe Flash Player for Android, go
to Settings > Applications > Manage Applications > Adobe Flash
Player x.x.
To verify the version of Adobe AIR installed on your system, follow the instructions in the Adobe AIR TechNote.
Articles on Oracle's Java Patches are few as of this writing, all I have managed to find is the download page for Java. There are links to the "Release Notes" pages for Java 6 and 7 on the download page:
- Java SE Downloads
Java SE 7u10
This releases brings in key security features and bug fixes. Oracle strongly recommends that all Java SE 7 users upgrade to this release.
Friday, September 7, 2012
Uninstall or downgrade Java, update Flash Player and your PDF Reader
1. Uninstall Java or go back to version 6. If you have Java installed on your computer and don't need it, UNINSTALL IT. There is an unpatched flaw in the all releases of version 7 which can be used in drive-by downloads to infect your computer just by visiting a hacked or malicious website. Check your version number here: Verify Java Version If you must use Java for any reason, I recommend uninstalling version 7 and getting version 6u35, which does not have the same flaws. If you have to have it for some reason, disable it in your browser except when needed. More below, and please feel free to email me (with your browser version) if you need help disabling Java.
2. Update Flash Player (or uninstall it). Flash Player, required for Youtube and other videos, is now at version 11.4.x for Windows (different version numbers for Mac, Linux, and Android) If you have it and are not at the current version, update it ASAP. Check your version number here: Adobe Flash Player.
3. Update your PDF Reader. My current PDF Reader is Sumatra PDF (v2.1.1(, but I also have the latest Foxit Reader (v5.4) installed. Both were updated this summer. If you still have Adobe Reader, you should be at version 9.5.2 or 10.1.4 as earlier versions have known "in the wild" exploits against them.
4. Do Windows Updates. If you do not have Windows Update set to automatic, you need to update Windows. Several critical issues were fixed in the August and September Patch-Tuesday events. See these ISC pages (July and August) for more technical details or these ZDNet pages (July and August) and Krebs on Security pages (July and August) for user-friendly discussions.
5. Update Apple Remote Desktop. Apple Remote Desktop, which many Mac users use to connect to their home or office computer while on the road, would connect insecurely without informing the remote user.
Java Runtime Engine
30 August 2012 (5 September 2012 for Apple)
- Oracle Security Alert for CVE-2012-4681
- Oracle Java Runtime Environment 6u35 Downloads
- Oracle Java Runtime Environment 7u7 Downloads
More info here:Pages about the unpatched new vulnerability reported after 7u7 was released are here:
- ISC Diary | Quick Bits about Today's Java 0-Day
- ISC Diary | Oracle Releases Java Security Updates
- Oracle issues emergency fix for Java security vulnerabilities - SC Magazine
- Security Fix for Critical Java Flaw Released — Krebs on Security
- Apple Releases Fix for Critical Java Flaw — Krebs on Security
NOTE 1: download the OFFLINE installer, not the ONLINE installer. The "online installer" often comes with additional installed-by-default crapware like "McAfee Security Scanner" or the Ask toolbar" while the "offline installer" does not.
- Java Users Still Not Safe, Experts Report New Vulnerability to Oracle (Exclusive) - Softpedia
- Disable Java NOW, users told, as 0-day exploit hits web * The Register
- Warning on critical Java hole - The H Security: News and Features
- Java zero day vulnerability actively used in targeted attacks | ZDNet
Security researchers from FireEye, AlienVault, and DeependResearch have intercepted targeted malware attacks utilizing the latest Java zero day exploit. The vulnerability affects Java 7 (1.7) Update 0 to 6. It does not affect Java 6 and below.
NOTE 2: after you update Java, home users should go to the Control Panel and change the "Check for updates" frequency from the default (once a month) to "Daily".
NOTE 3: Even Microsoft says Update Java or kill it (an article on ZDNet).
Adobe Flash Player
21 August 2012
Adobe - Security Bulletins: APSB12-19 - Security updates available for Adobe Flash PlayerAdobe has released security updates for Adobe Flash Player 11.3.300.271 and earlier versions for Windows and Macintosh, Adobe Flash Player 11.2.202.236 and earlier versions for Linux, Adobe Flash Player 11.1.115.11 and earlier versions for Android 4.x, and Adobe Flash Player 11.1.111.10 and earlier versions for Android 3.x and 2.x. These updates address vulnerabilities that could cause a crash and potentially allow an attacker to take control of the affected system.Even though Adobe has abandoned Linux a security update is available.
For more info, see these pages:
Firefox 15.0.1
7 September 2012
Mozilla has released Version 15.0.1 of the Firefox browser. This version fixes a bug with Private Browsing mode.
Your PDF reader should be one of these (more below):
- SumatraPDF 2.1.1
- Foxit Reader 5.4
- Adobe Reader 9.5.2 or 10.1.4
Sumatra PDF v2.1.1Sumatra PDF is a very lightweight PDF reader which is my current preferred reader. Get it here:
- Download page
- Direct link to Installer
- Direct link to Portable version (a single executable that can be run e.g. from USB drive and doesn't write to registry)
Foxit Reader 5.4.27 September 2012
The free Foxit PDF Reader has been updated to Version 5.4.2.0901. This update adds support for DocuSign and Microsoft SharePoint Server, as well as a range of bug fixes.
See: Foxit Reader Security BulletinSUMMARY
Foxit Reader 5.4 fixed an issue where Foxit Reader may call and run malicious code in the Dynamic Link Library (DLL) file. Attackers could place the infected DLL file, whose name is the same as the system DLL in the Windows prior search path, and then enable Foxit Reader to call the malicious file.
Affected VersionsFixed in Version
- Foxit Reader 5.3.1.0606 and earlier.
- Foxit Reader 5.4
Note that the Enterprise Foxit Reader has not been updated since version 5.1 and should be removed from your system. Replace it with SumatraPDF or the home-user version of Foxit Reader.
Adobe Reader 9.5.2 or 10.1.414 August 2012
See:
Adobe - Security Bulletins: APSB12-16 - Security update available for Adobe Reader and AcrobatAdobe has released security updates for Adobe Reader and Acrobat X (10.1.3) and earlier versions for Windows and Macintosh. These updates address vulnerabilities in the software that could cause the application to crash and potentially allow an attacker to take control of the affected system.Get Adobe Reader installers and patches here: Adobe - Adobe Reader : For Windows
Adobe recommends users update their product installations to the latest versions:
- Users of Adobe Reader X (10.1.3) and earlier versions for Windows and Macintosh should update to Adobe Reader X (10.1.4).
- For users of Adobe Reader 9.5.1 and earlier versions for Windows and Macintosh, who cannot update to Adobe Reader X (10.1.4), Adobe has made available the update Adobe Reader 9.5.2.
Apple Remote Desktop
20 August 2012
Apple Remote Desktop, which many Mac users use to connect to their home or office computer while on the road, would connect insecurely even when told to connect securely.
Apple Remote Desktop 3.6.1When connecting to a third-party VNC server with "Encrypt all network data" set, data is not encrypted and no warning is produced. This issue is addressed by creating an SSH tunnel for the VNC connection in this configuration, and preventing the connection if the SSH tunnel cannot be created.
Thursday, June 28, 2012
Non-Microsoft patches for June
If you run iTunes, you need to update it.
One final story got left out of my last blog post about Microsoft updates. It's the first link below. If you run IE, PATCH NOW!
There are some additional security patches which may be of minor interest. On Monday, May 14, 2012, I posted a notice that Adobe to patch Illustrator, Photoshop, and Flash Pro CS5.x for free, Well, they have finally issued patched the last member of the three, Flash Pro. Google's Chrome browser got patched again, but since it auto-updates you should already be using this version. If you use WinAmp, you should patch to the latest version. Links are below.
- Bad guys using unpatched Internet Explorer flaw to hack Gmail accounts
Last week, Google warned its users that “state-sponsored attacks” were under way aimed at accessing Gmail accounts. Those targeted saw a message at the top of their Gmail inboxes warning that “state-sponsored attackers may be attempting to compromise your account or computer”.
At the time, Google was mum on the specific exploit, but on Wednesday Microsoft provided details in a security advisory, and they’re not pretty. Google also discussed the exploit in its own blog post.
Cyberscum are taking advantage of an unpatched, zero-day flaw in Windows XP or later to run malicious code on the user’s computer. The code is planted when the user visits a poisoned website using any version of Internet Explorer. The exploit also works through Microsoft Office documents.
This is a silent, drive-by download. If you’re attacked, you may not know it . . . unless you get that cryptic message atop your Gmail inbox.
On Tuesday, Microsoft release some security fixes for Windows, but a patch for this flaw was not included. Don’t think your Windows PC is protected if you conscientiously updated this week. However, Microsoft has released a “Fix It For Me” item that will block the exploit. All Windows users should apply this, even if you don’t use IE or Gmail, but keep in mind it does not fix the underlying flaw in Windows. A future patch – possibly one released before the next Patch Tuesday – will be released for a true fix.
- Apple, Oracle Ship Java Security Updates — Krebs on Security
Wednesday, June 13th, 2012
There must have been some rare planetary alignment yesterday, because the oddest thing happened: Apple and Oracle both shipped software updates for the same Java security flaws on the very same day. ... The update Oracle released yesterday, Java 6 Update 33 and Java 7 Update 5, fixes at least 14 security flaws in the oft-attacked software that is installed on more than three billion devices worldwide. Apple’s Java update brings Java on the Mac to 1.6.0_33, and patches 11 of the 14 security vulnerabilities that Oracle fixed in Tuesday’s release. It’s unclear whether those other three flaws simply don’t exist in the Mac version of Java, but we’ll take progress where we can get it. - ISC Diary | Java 7u5 and 6u33 released
Published: 2012-06-12,
Oracle is releasing Java 7 update 5 and Java 6 update 33 today.Updated after Oracle released the vulnerability details.
- Release notes for 6u33
- Release notes for 7u5
- Downloads
- Advisory (contains their risk matrix)
- More verbose version of their risk matrix
Unfortunately it's all still made to be useless to determine what the problems are with the software and perform your own risk assessments.
Just note there are CVSS scores of 10 in there, and in the past months we saw what slacking on patching Java can do (Ref: the recent Apple Mac OS X malware), so just patch this on a rather urgent time schedule due to lack of detailed descriptions.
Update:
My words above were barely written or I got the notification of Apple that they are releasing Java for OS X 2012-004 and Java for Mac OS X 10.6 Update 9 today as well. This brings them in line with the updates to 1.6.0_33 above as well as implementing the deactivation of the Java browser plugin and Java Web Start if they remain unused for 35 days to Snow Leopard and deactivating the Java browser plugin and Java Web Start if they do not meet the criteria for minimum safe versions (on Both Lion and Snow Leopard.
- Adobe fixes Flash Player for Firefox to stop crashes | Applications - InfoWorld
June 22, 2012
Adobe yesterday updated Flash Player to solve a weeks-long problem for users of Mozilla's Firefox browser.
The update, Flash Player 11.3.300.262, was released Thursday and applies only to Firefox on Windows.
Since Adobe shipped an update to Flash Player to 11.3 two weeks ago, users of Firefox, including older editions as well as the current Firefox 13, had reported crashes when trying to access Flash content.
- Release Notes | Flash Player 11.3 AIR 3.3
June 21, 2012. Welcome to Adobe® Flash Player® 11.3 and AIR® 3.3. This release includes bug fixes related to stability with Firefox on Windows
- ISC Diary | Apple iTunes Security Update
Published: 2012-06-12
Apple announced a new update for iTunes today. Per APPLE-SA-2012-06-11-1, this update addresses a problem when importing a maliciously crafted m3u playlist within iTunes and a problem within WebKit when visiting a maliciously crafted website.
The bulletin is available at http://support.apple.com/kb/HT5318. - About the security content of iTunes 10.6.3
- Adobe - Security Bulletins: APSB12-12 Security bulletin for Adobe Flash Professional
Last Updated: June 25, 2012
Adobe released a security update for Adobe Flash Professional CS5.5 (11.5.1.349 and earlier) for Windows and Macintosh. This update addresses a vulnerability that could allow an attacker who successfully exploits this vulnerability to take control of the affected system. - Chrome 20 fixes 20 security vulnerabilities | ZDNet
By Dancho Danchev | June 27, 2012, 10:59am PDT
Summary: In its latest browser release, 20.0.1132.43, Google’s Chrome fixes 20 security vulnerabilities, none of which are critical. - Winamp 5.63 fixes four critical security vulnerabilities | ZDNet
By Dancho Danchev | June 27, 2012, 10:30am PDT
Summary: Winamp version 5.63 fixes four critical security vulnerabilities.As originally reported in Winamp’s release announcement, version 5.63 fixes four critical security vulnerabilities. Successful exploitation of the vulnerabilities allows execution of arbitrary code. For the exploitation to take place, a user running an outdated version of Winamp, would have to open a specially crafted . AVI video file.
More details about the vulnerability can be found in this Secunia advisory.
Microsoft Updates for June: Critical PATCH NOW fix for IE, an additional manual FixIt needed
Windows Updates for June, 2012, included some critical patches, and one that ISC rated PATCH NOW! to fix a soon-to-be-in-the-wild flaw in Microsoft Internet Explorer and Microsoft Office. If you have not patched any of your systems where you use IE or Office, you need to do so ASAP. In addition, Microsoft issued a separate advisory about a "browse-and-get-owned flaw that can be triggered when an Internet Explorer user on any supported version of Windows visits a specially crafted Web page. Microsoft does not have an official patch available yet for this flaw, but it has issued a FixIt tool workaround that effectively disables the vulnerable component"
Not quite one week later ZDnet published an article stating that the IE/Office vulnerability was now available to hackers. Many other security sites are reporting on these issues. Lots of useful links and technical info are below.
If you use IE for your Internet surfing, you should run Windows Update AND run the MS FixIt tool workaround ASAP.
(EDIT: Add final link to MS Blog entry about the FixIt.)
- ISC Diary | Microsoft June 2012 Black Tuesday Update - Overview
- Patch Tuesday: Microsoft raises alert for dangerous IE, Windows flaws | ZDNet
By Ryan Naraine | June 12, 2012, 2:13pm PDT
Summary: Microsoft expects to see exploit code targeting at least one of the vulnerabilities within the next 30 days.
Microsoft today warned that cyber-criminals could soon aim exploits at critical security flaws in Internet Explorer browser and Windows to hijack and take complete control of vulnerable machines.
The warning comes as part of this month’s Patch Tuesday where Microsoft released 7 bulletins with fixes for at least 26 documented vulnerabilities affecting the Windows ecosystem.
The company is urging users to pay special attention to MS12-037 and MS12-036, which provides cover for “remote code execution” vulnerabilities that could be used in worm attacks and drive-by downloads without any user interaction. - Microsoft Patches 26 Flaws, Warns of Zero-Day Attack — Krebs on Security
Microsoft today released updates to plug at least 26 separate security holes in its Windows operating systems and related software. At the same time, Microsoft has issued a stopgap fix for a newly-discovered flaw that attackers are actively exploiting.
...
In a separate advisory published today, Microsoft warned that it is aware of active attacks that leverage a vulnerability in Microsoft XML Core Services 3.0., 4.0, 5.0. and 6.0. This is a browse-and-get-owned flaw that can be triggered when an Internet Explorer user on any supported version of Windows visits a specially crafted Web page. Microsoft does not have an official patch available yet for this flaw, but it has issued a FixIt tool workaround that effectively disables the vulnerable component. The vulnerability was discovered by Google, which said it saw the flaw being exploited in the wild in targeted attacks.
- Google Online Security Blog: Microsoft XML vulnerability under active exploitation
Tuesday, June 12, 2012 12:53 PM
Posted by Andrew Lyons, Security Engineer
Today Microsoft issued a Security Advisory describing a vulnerability in the Microsoft XML component. We discovered this vulnerability—which is leveraged via an uninitialized variable—being actively exploited in the wild for targeted attacks, and we reported it to Microsoft on May 30th. Over the past two weeks, Microsoft has been responsive to the issue and has been working with us. These attacks are being distributed both via malicious web pages intended for Internet Explorer users and through Office documents. Users running Windows XP up to and including Windows 7 are known to be vulnerable.
As part of the advisory, Microsoft suggests installing a Fix it solution that will prevent the exploitation of this vulnerability. We strongly recommend Internet Explorer and Microsoft Office users immediately install the Fix it while Microsoft develops and publishes a final fix as part of a future advisory.
- Attack code published for 'critical' IE flaw; Patch your browser now | ZDNet
By Ryan Naraine | June 18, 2012, 3:09am PDT
Summary: Microsoft has confirmed that this flaw is being used in “limited attacks” but the company has not (yet) updated its MS12-037 bulletin to make it clear that public exploit code is now widely available.
- ISC Diary | Microsoft Security Advisory 2719615 - MSXML - CVE-2012-1889
Published: 2012-06-12,
Several readers mentioned that Microsoft today issued a Security advisory regarding Microsoft XML Core Services (MSXML). This is in response to active exploitation.
The issues affects Office 2003 and 2007 on all versions of windows. All a user has to do to fall victim is visit the wrong website using IE.
Microsoft has issued a fixit for it in the form of an msi file (see the KB 2719615 link below).
Alternative strategies would be to use browsers that do not support ActiveX, or disable the support in IE.
Links:
- Active Zero-Day Exploit Targets Internet Explorer Flaw | Blog Central
Tuesday, June 12, 2012 at 1:02pm by Yichong Lin
- MSXML: Fix it before fixing it - Security Research & Defense - Site Home - TechNet Blogs
13 Jun 2012 6:30 PM
Yesterday, Microsoft has released Security Advisory target="_blank"2719615, associated to a vulnerability in Microsoft XML Core Services. We want to share more details about the issue and explain the additional workarounds available to help you protect your computers.
Friday, June 8, 2012
Adobe Patches: Flash Player, Illustrator CS5, and Photoshop CS5 (12.0)
Almost a month ago (on Monday, May 14, 2012), I posted a notice that Adobe to patch Illustrator, Photoshop, and Flash Pro CS5.x for free, Well, they have patched Illustrator and Photoshop CS5.x now. Flash Pro is not patched yet. If you have either of these products, I recommend you apply the patches as the Bad Guys have had almost a month to reverse-engineer the fixes that went in to CS6.
Critical Security Fixes for Adobe Flash Player — Krebs on Security
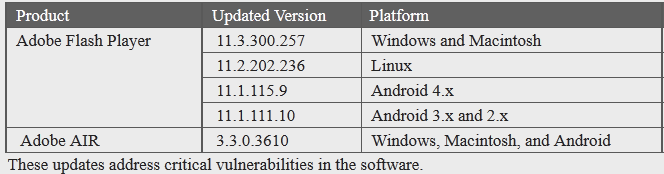
Adobe has released a critical update to its Flash Player software that fixes at least seven security vulnerabilities in the program. The new version also extends sandboxing protection to Mac OS X users browsing the Web with Mozilla Firefox.Adobe - Security Bulletins: APSB12-14 - Security updates available for Adobe Flash PlayerThe update, Flash Player 11.3, plugs at least seven security holes in Flash Player and Adobe Air. The company warns that attackers could use these flaws to crash the applications and seize control over unpatched systems. Flash updates are available for Windows, Mac, Linux and Android systems. Adobe AIR patches are available for Windows, Mac and Android platforms. See the chart below for the latest, patched versions numbers for each platform.
Adobe released security updates for Adobe Flash Player 11.2.202.235 and earlier versions for Windows, Macintosh and Linux, Adobe Flash Player 11.1.115.8 and earlier versions for Android 4.x, and Adobe Flash Player 11.1.111.9 and earlier versions for Android 3.x and 2.x. These updates address vulnerabilities that could cause a crash and potentially allow an attacker to take control of the affected system.
Adobe - Security Bulletins: APSB12-09 - Security bulletin for Adobe Illustrator
Adobe released security updates for Adobe Illustrator CS5 (15.0.x) and Adobe Illustrator CS5.5 (15.1) for Windows and Macintosh. These updates address vulnerabilities that could allow an attacker who successfully exploits these vulnerabilities to take control of the affected system.Adobe - Security Bulletins: APSB12-11 Security bulletin for Adobe Photoshop
Adobe released security updates for Adobe Photoshop CS5 (12.0) and Adobe Photoshop CS5.1 (12.1) for Windows and Macintosh. These updates address vulnerabilities that could allow an attacker who successfully exploits these vulnerabilities to take control of the affected system.